Automating the VMware Carbon Black Local Mirror Server configuration for Windows
This blog post describes the automation of the VMware Carbon Black Local Mirror Server for Windows, including the necessary configuration for pointing the sensors to the VMware Carbon Black Local Mirror Server.
Getting Started
Before I continue, I want to point out that there are some great Getting Started articles for VMware Carbon Black, written by my colleagues.
- Set up Carbon Black Cloud Workload Protection – Age Roskam
- Carbon Black Workload Protection and VMware Tools compatibility – Wesley Geelhoed
- Installing Carbon Black sensors – Age Roskam
- Carbon Black and non-persistent VDI – Age Roskam
- Securing devices with VMware Carbon Black and Workspace ONE UEM – Age Roskam
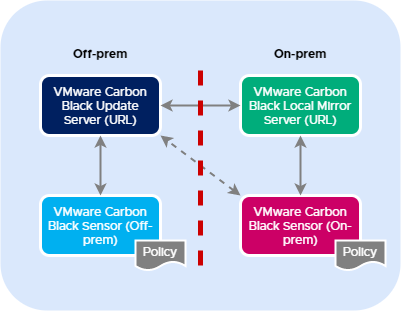
The Local Mirror Server Concept
The Local Mirror Server may be used in situations where the sensors may not have direct internet access for updating their signature updates, or where you want to force sensors to update from an internal source.
The Local Mirror Server is placed in the on-prem datacenter, where it receives its updates from the VMware Carbon Black update server (URL). Sensors that are seen as on-prem may receive signature updates from this Local Mirror Server and may fall-back to the VMware Carbon Black update server (URL), if required. The following diagram provides a global overview of the concept.
Configuring the Local Mirror Server (manually)
VMware Carbon Black has a well written knowledge base article available, which describes the required steps for configuring the Local Mirror Server manually.
CB Defense: How to configure a Local Mirror (Windows)
This article contains the following steps.
- Creating the folder structure, and mirror files unzipping.
- Creating the scheduled task.
- Creating the IIS website.
Configuring the Local Mirror Server (automated)
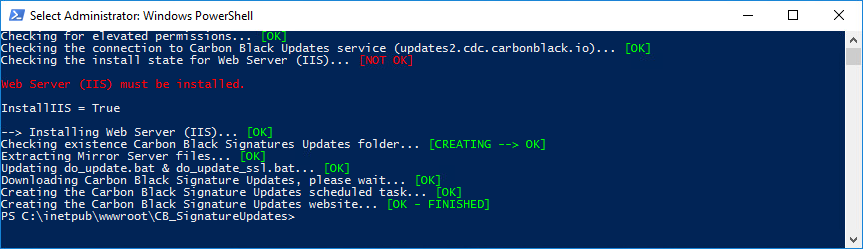
Based on the required steps from the article mentioned in the previous chapter (CB Defense: How to configure a Local Mirror (Windows)), I have written a PowerShell script that automates all those steps. This script is called Create-CBWinLocalMirror.ps1, and is publicly available on GitHub.
Create-CBWinLocalMirror.ps1 accepts all necessary parameters to fully automate the Local Mirror Server configuration, including the installation of the required IIS componentes, when requested.
Script parameters
Create-CBWinLocalMirror.ps1 requires the following parameters (taken from the script’s synopsis).
.PARAMETER CBUpdatesURL
Specifies the Carbon Black external URL from which the Carbon Black Local Mirror server receives the updates.
.PARAMETER CBUpdatesFolderName
Specifies the name for the folder in which the Carbon Black Local Mirror server files are placed.
.PARAMETER CBUpdatesScheduledTaskName
Specifies the name for the scheduled task that is used for receiving the updates.
.PARAMETER CBUpdatesIntervalMinutes
Specifies the updates interval in minutes.
.PARAMETER CBUseSSL
Specifies if updates must be received using SSL.
.PARAMETER CBUpdatesWebSiteName
Specifies the name for the website in IIS.
.PARAMETER CBZipFile
Specifies the name for the ZIP file that contains the Carbon Black Local Mirror server files.
.PARAMETER HostNameFQDN
Specifies the fully qualified domain name (FQDN) used for the IIS website.
.PARAMETER InstallIIS
Specifies if IIS must be installed.
Full parameters help is available using the following command.
help .Create-CBWinLocalMirror.ps1 -full
Script usage example
Create-CBWinLocalMirror.ps1 -CBUpdatesURL updates2.cdc.carbonblack.io -CBUpdatesFolderName CB_SignatureUpdates -CBUpdatesScheduledTaskName CB_SignatureUpdates -CBUpdatesIntervalMinutes 60 -CBUseSSL $False -CBUpdatesWebSiteName CB_SignatureUpdates -CBZipFile cbdefense_mirror_win_x64_v3.0.zip -HostNameFQDN domain.lab.local -InstallIIS $True
Testing the Local Mirror configuration
To test the Local Mirror functionality, we will check two items.
- Scheduled task (i.e., are the updates coming in?)
- Website (i.e., is the Local Mirror reachable, and presenting the signature updates?)
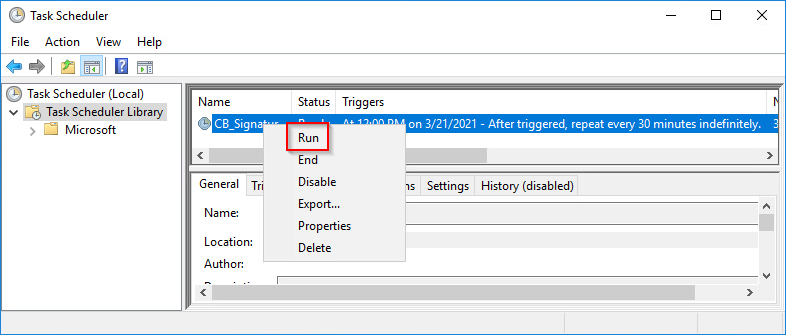
Scheduled task
The scheduled task downloads the signature updates from the VMware Carbon Black updates server (URL). To make sure that this tasks runs without errors, run this task manually.
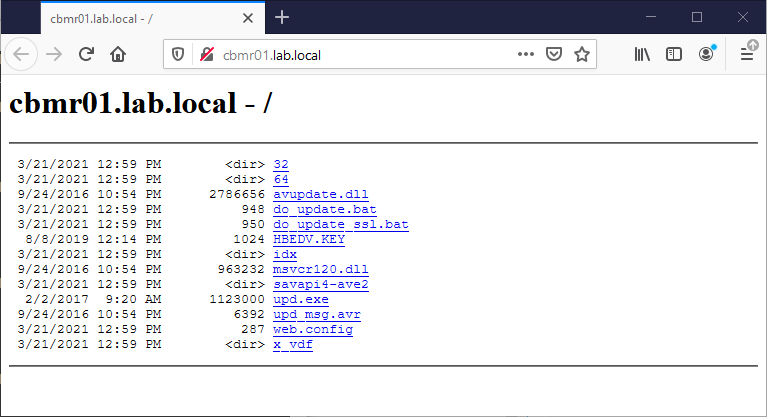
Website
The sensors that use the Local Mirror Server, must be able to reach the Local Mirror Server website. Open a web browser, preferrably within the same subnet as the sensors, and open the Local Mirror Server website URL.
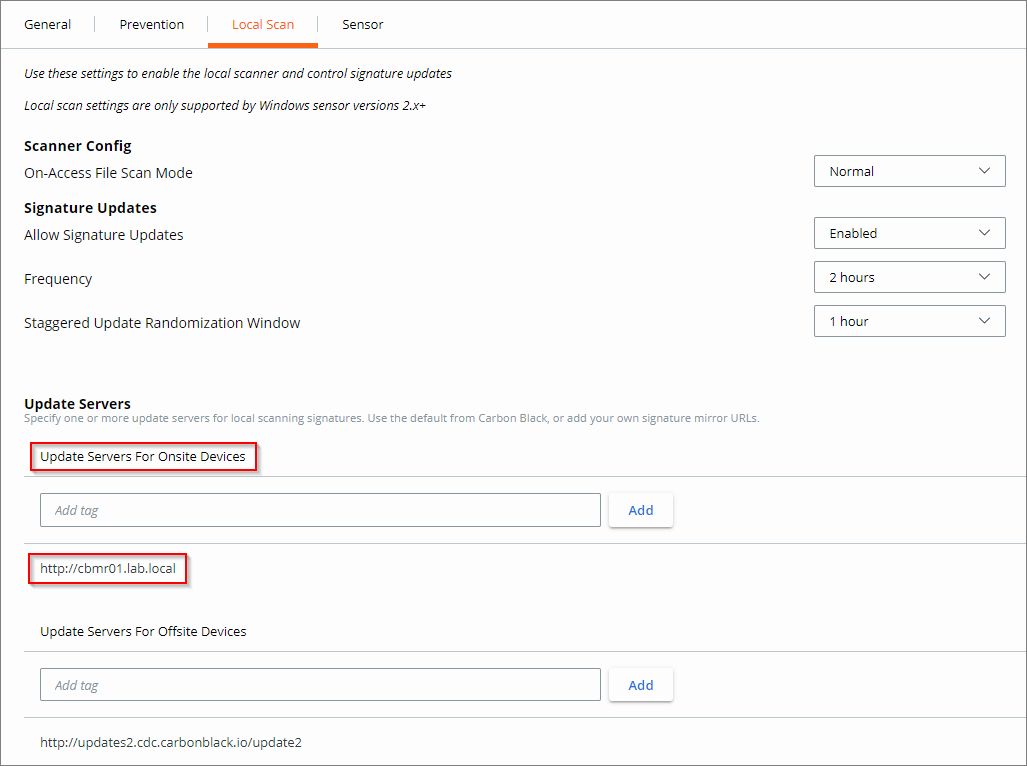
Configuring the policy
Within Carbon Black Cloud, create or edit an existing policy, in which you configure the on-prem (or onsite) sensors (devices) to point to your Local Mirror Server website (URL).
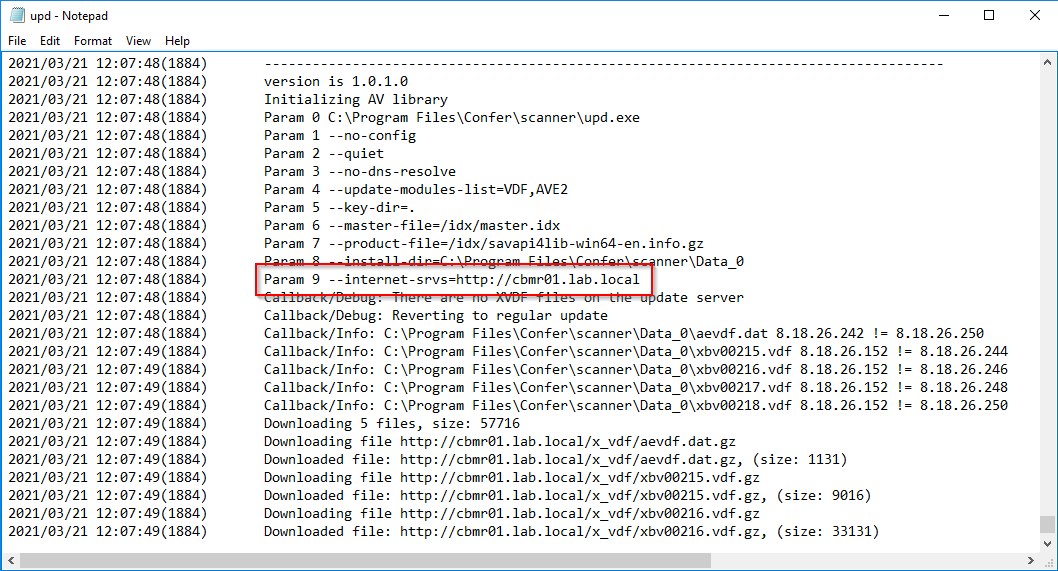
Checking the log file
To check if the sensor is using the Local Mirror Server for its signature updates, open the upd.log file on the sensor. This file can be found in C:\ProgramData\CarbonBlack\Logs.
I hope this blog post was informative. If you have any questions or comments, please reach out on Twitter or LinkedIn.